University it security strategy
The Guidance on Information Security with Mobile Devices sets out the practices and safeguards that staff, partner staff, contractors and researchers must adopt when accessing or moving university data, including email, around on portable media. We have the answers to your questions, find all the advice and support in one place. Applications, Offers and Enrolments — Transparency Information. Data Protection. Modern Slavery. Environmental Sustainability. Find your course. Browse your subject areas.
Civil Engineering. Dental Technology. Fashion and Textiles. Film FX. Graphic Design. Medical Biology.
Information Security Policy / Document / Victoria University Policy Library
Social Work. Postgraduate Courses. Study with an Off-Campus Partner. Download a Brochure. Chat with Staff. Career Development Masters. Studying at Bolton. Life at Bolton. Student Support. Visit the Bolton Students Union. Chat to our Students. University Bicycle Scheme. Continuous adaptation: Review and improve information security management in response to security incidents and keep pace with changes to the University, information technology, security technology and the threat landscape.
Engage and collaborate: Build and engage in mutually beneficial partnerships throughout the cyber and higher education industries to enhance protection against common threats. Automate first: Utilise automated processes where feasible to enable consistent, accurate and timely deployment of security controls with reduced dependence on manual labour.
Achieving our strategic objectives will help UQ improve its cyber security maturity. Cyber security awareness for UQ students and staff. Skip to menu Skip to content Skip to footer. Site search Search.
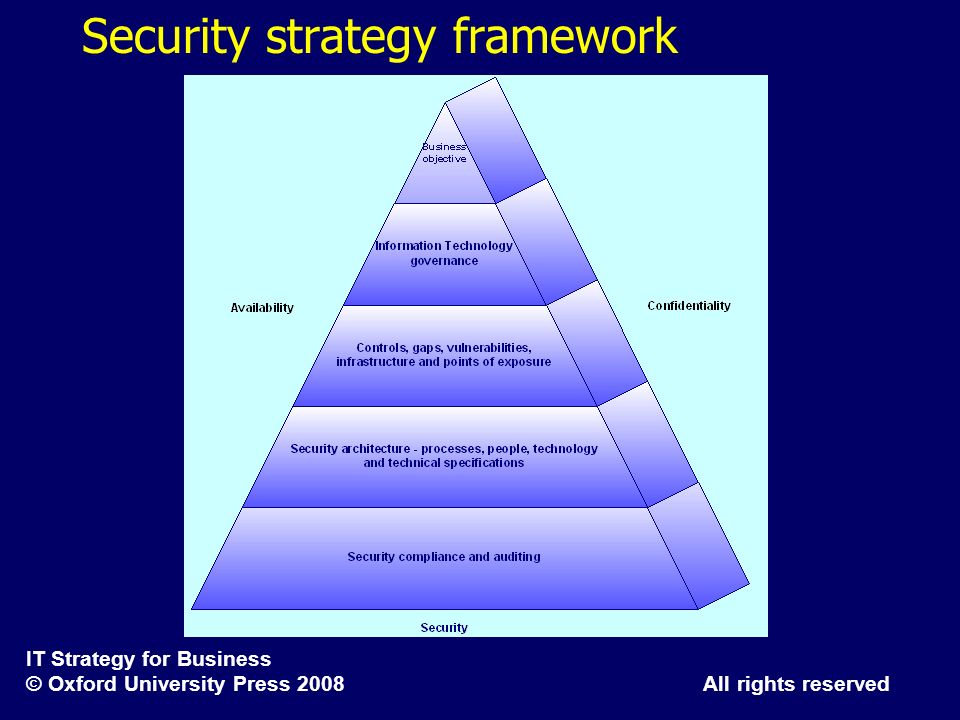
Top Menu Banner
Site search Search Menu. Cyber Security Strategy. Our goal Our principles Key objectives Success measures. Key objectives 1. Provide IT services that enable business processes without compromising security. Where possible, adopt security solutions that protect UQ without detracting from the digital experience. E-Health Queensland. Cyber Aware. MurdockCheng Legal Practice. Cooper Mills Lawyers.
INTR71-102: Security and Strategy
Water Corporation. Teron Labs. Customer Owned Banking Association.
Risk Frontiers. La Trobe University. Access Now. Wise Law. Cyber Institute ANU. Preston de Guise. Noetic Group. ITS Australia. National Australia Bank. Tanya Cumpston. Central Queensland University. City of Joondalup. Universities Australia. Price Waterhouse Coopers. Monash University. Ernst and Young.
Oceania Cyber Security Centre.
Commonwealth Bank of Australia. The Group of Eight.
- forex go market.
- forex analysis gbp usd!
- You are here:.
- Top Menu Banner?
- binary options 90.
- forex pairs that move together?
- buy forex cash online?
The University of Melbourne. Deakin University. Telstra Corporation Limited. Sapien Cyber. RMIT University. Digital Industry Group Inc. VeroGuard Systems. Office of the Australian Information Commissioner.
Description
Department of Premier and Cabinet - Tasmania. ANZ Bank. Deliotte Australia. Cyber Security Cooperative Research Centre. Lockheed Martin Australia. Cisco Systems Australia.